Hardening security on Kubernetes with KubeArmor
KubeArmor provides runtime protection on Kubernetes using policies. It uses eBPF and Linux Security Modules (LSM). It can restrict any malicious or unwanted behavior by cluster uses.
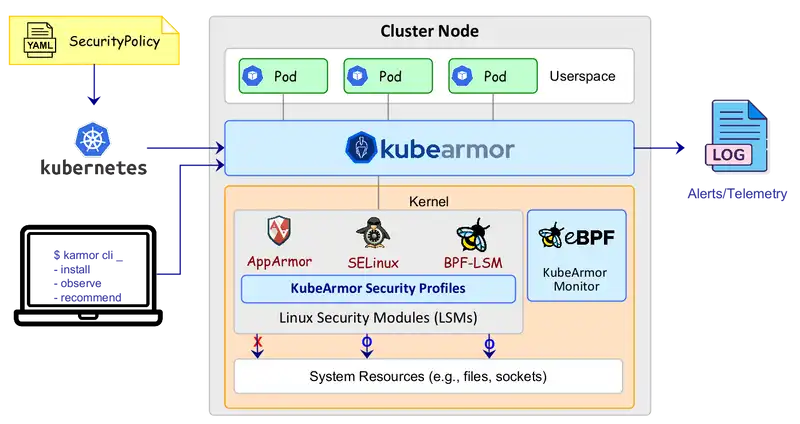
As you can see the Kubearmor is placed between the kernel and running pods. In this placement, it can filter out restricted actions. On the cluster.
KubeArmor is currently in the Sandbox category on the cncf.io.
An example of a policy that restricts running ps in the active containers is given below.
apiVersion: security.kubearmor.com/v1
kind: KubeArmorPolicy
metadata:
name: ksp-group-1-proc-path-block
spec:
severity: 5
message: "block /bin/ps"
selector:
matchLabels:
group: group-1
process:
matchPaths:
- path: /usr/bin/ps
action:
BlockAfter applying it to the running cluster. When you try to exec ps in the containers it will block the action.
Let's start to see how to install karmor on the existing cluster. Pre requisite is to have running cluster. If you want to setup one you can check out the article:
We will go through the installation process of the KubeArmor, some neat policy examples, network hardening, and scanning of the current cluster with the KubeArmor which recommends policies automatically.
